Secure remote mailbox access
Protect Exchange mailboxes accessed through Outlook Web Access (OWA) and ActiveSync with UserLock. Monitor, control, and react to suspicious IIS sessions to prevent unauthorized access.
Unauthorized access to users’ Exchange mailboxes is a critical security concern.
With UserLock, administrators can monitor and control IIS-based sessions such as Outlook Web Access (OWA) or ActiveSync connections.
This ensures visibility and protection over all remote mailbox access.
The procedure applies to:
Exchange 2013
Exchange 2010
Exchange 2016 and later (see specific note below)
Before starting, ensure that:
✅️ The UserLock IIS Agent is deployed and configured on the Exchange server.
✅️ The IIS web applications (OWA, ActiveSync) are enabled on the monitored Exchange server.
Once the IIS Agent is installed on the Exchange server, connect to Outlook Web Access (OWA) using any account.
In the UserLock console ▸ Active sessions, you’ll see a new IIS session corresponding to the mailbox access.
If the user signs out of OWA and you refresh the Active Sessions view, the IIS session disappears, confirming the session tracking is active.
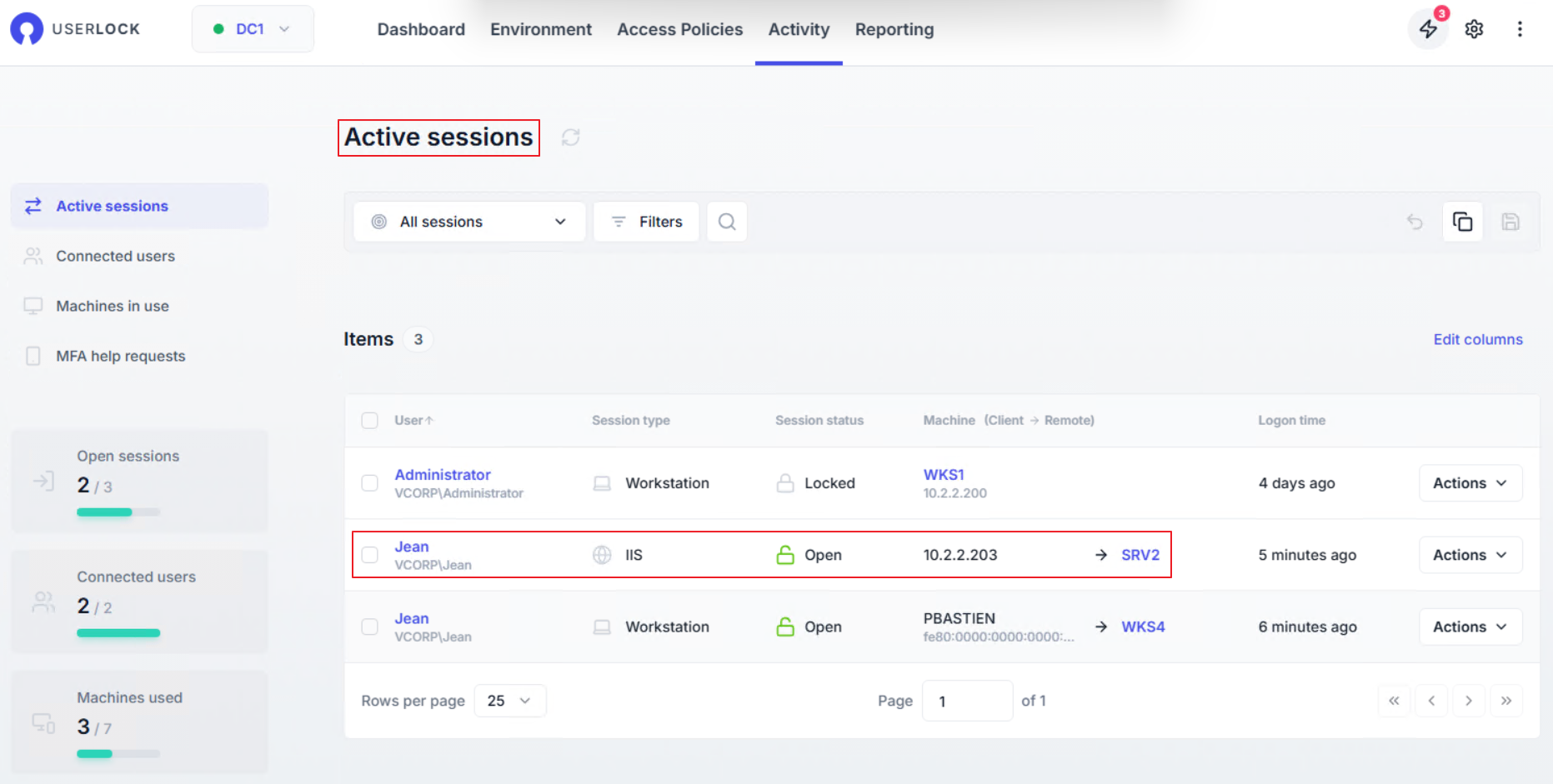
If a user’s mailbox is accessed from an unusual workstation or IP address, UserLock immediately makes it visible.
In the UserLock console, go to Activity ▸ Active sessions.
👉️ Example: if Jean signs in to Alice’s mailbox through OWA, the session appears under Alice’s name but from Jean’s workstation IP address.
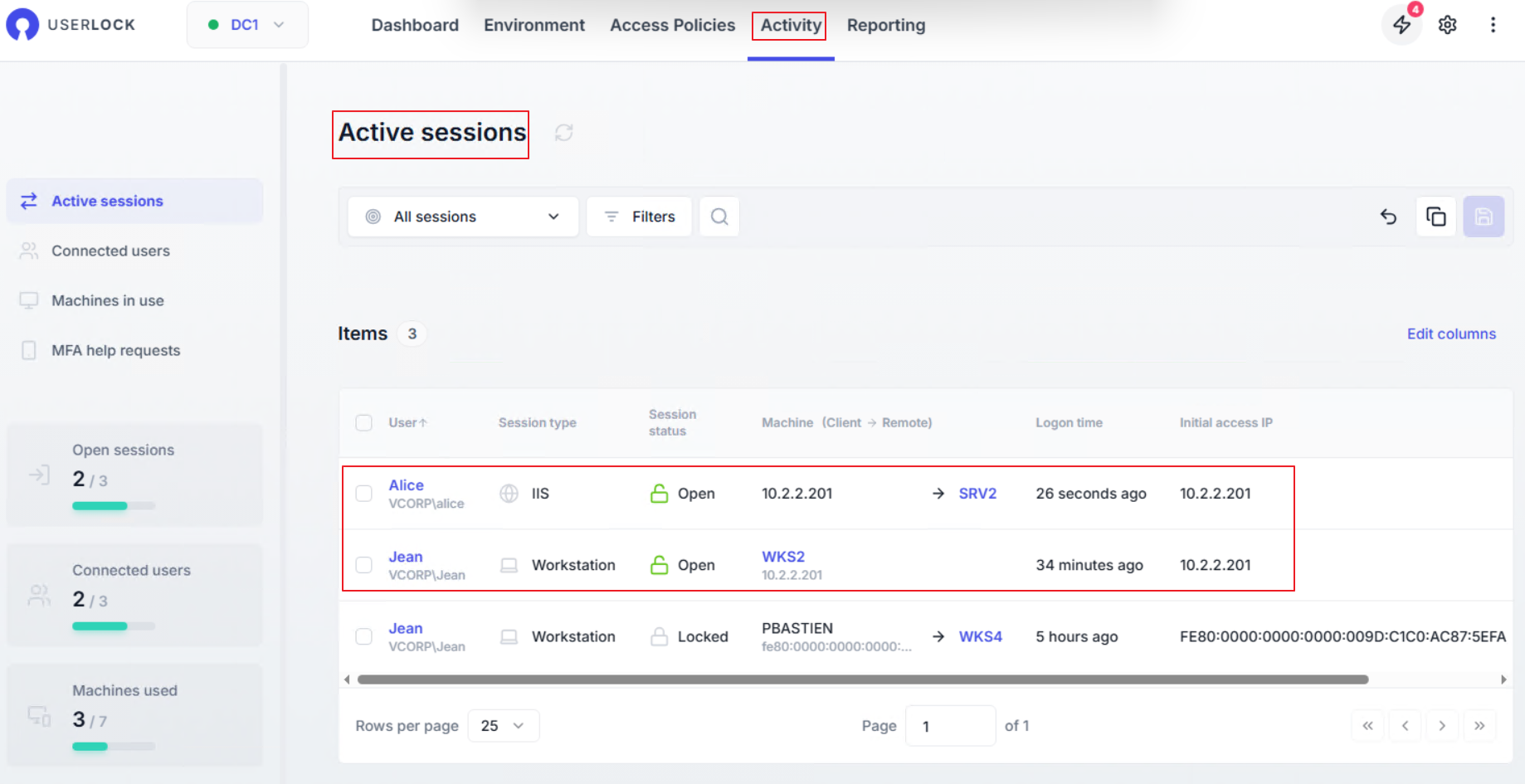
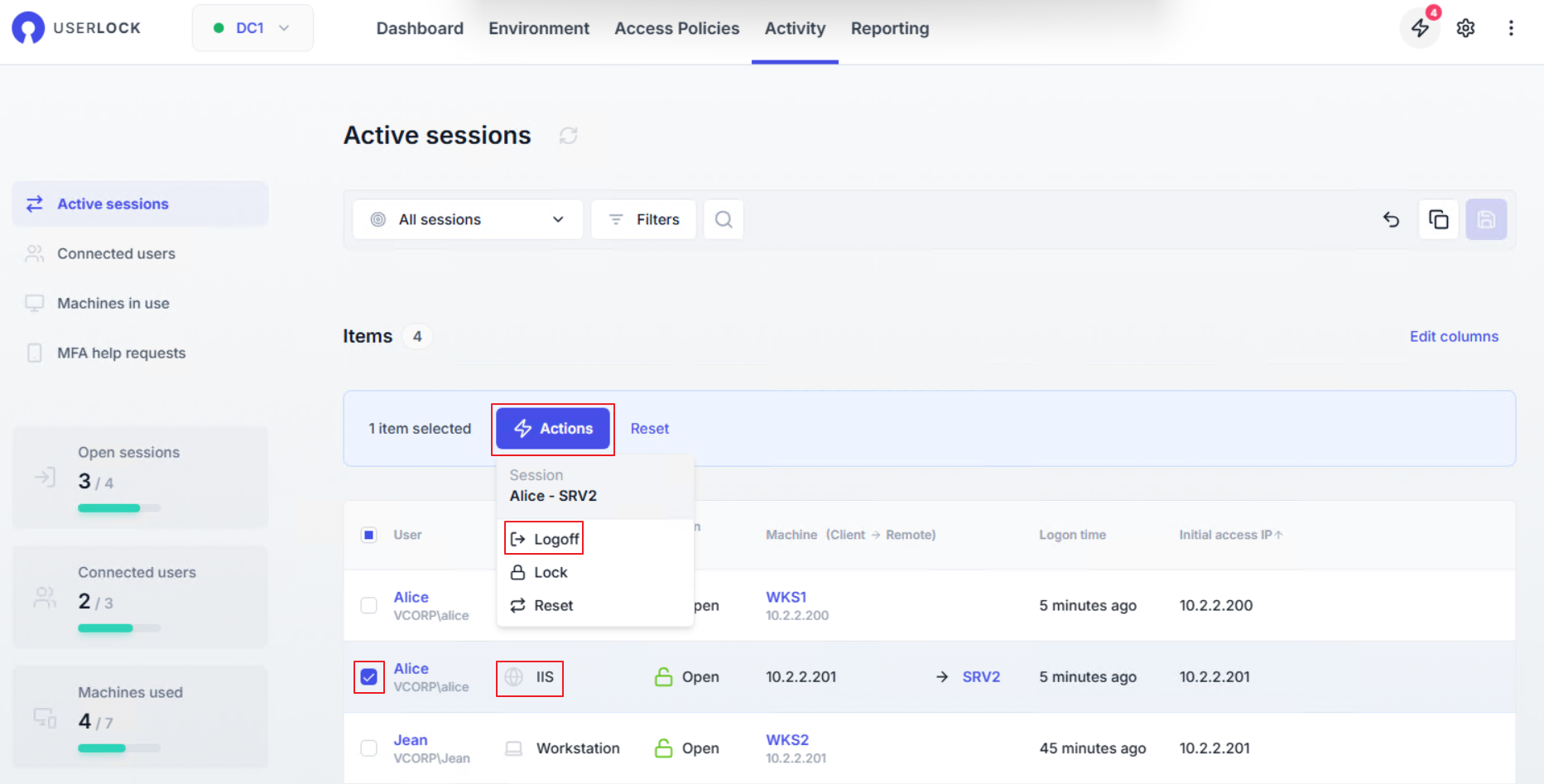
Identify the suspicious session.
Select it, then click Actions ▸ Logoff.
This immediately ends the unauthorized mailbox access.
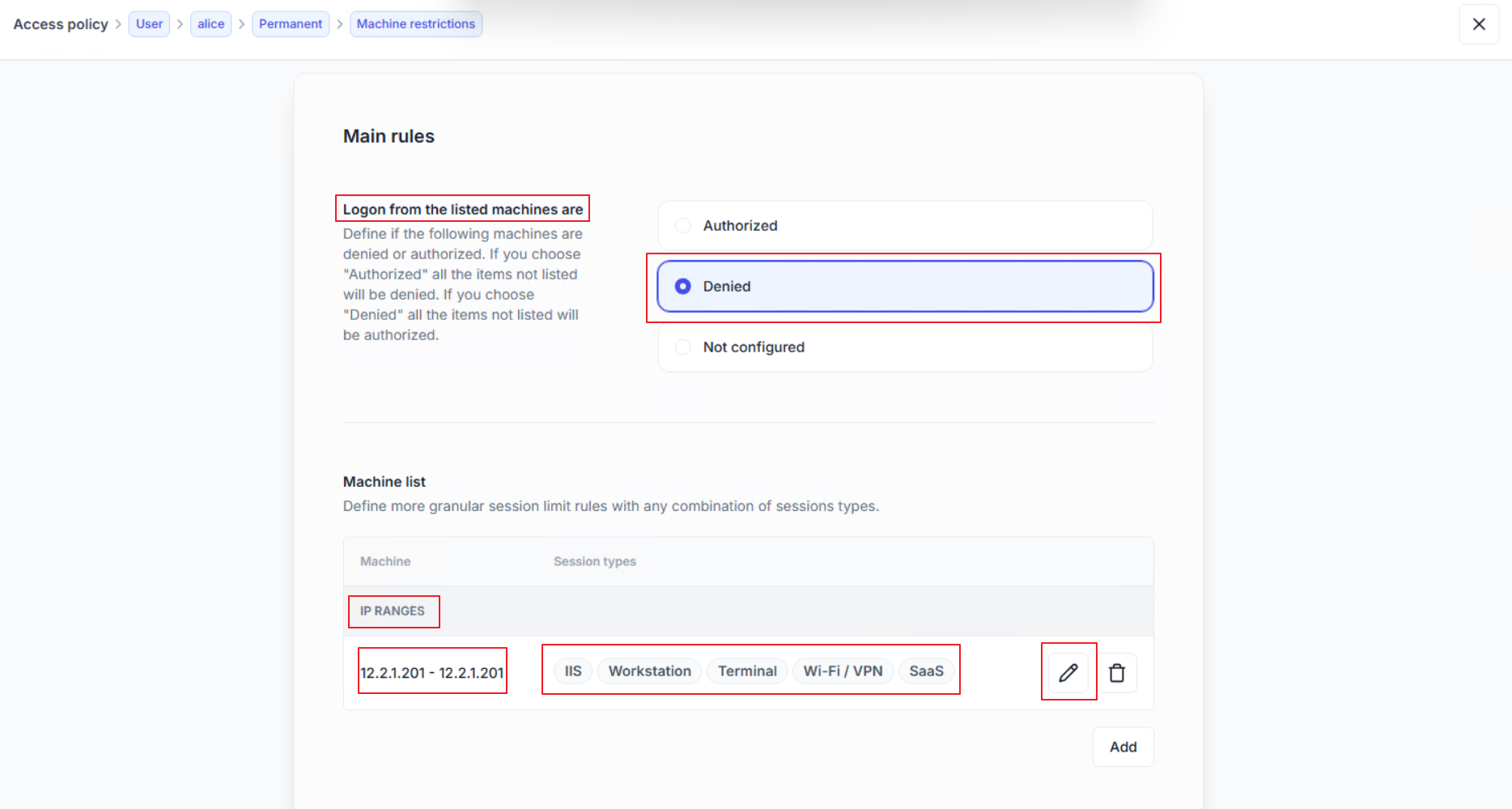
To prevent future unauthorized access, administrators can restrict IIS sessions by IP address.
In the console, open Access Policies from the top menu.
Edit an existing policy for your user, or create a new access policy (see Create an access policy for detailed steps).
In the policy editor, select the Machine restrictions section.
Set Logon from the listed machines are to Denied.
Click Add.
Select by IP range and enter the values (e.g.:
10.2.2.201to10.2.2.201for the example)Select Session types to IIS.
Click Continue then Save.
Jean is redirected to the OWA logon page.
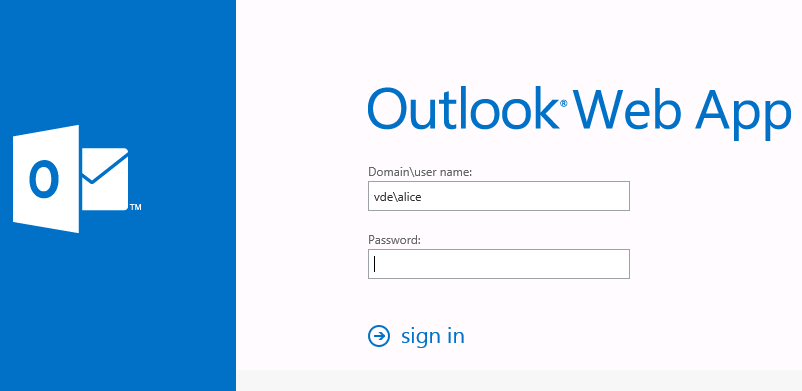
Any further attempt to log in using Alice’s credentials is denied.
The same procedure works on Exchange 2016 and later.
However, there is one specific point to note:
If you follow this procedure to the end, the IIS Agent will be configured only for the “OWA” and “Microsoft-Server-ActiveSync” applications.
With Exchange 2016 or higher, after any update, all HTTP modules (including the IIS Agent) configured only at the application level (not at the IIS root) are automatically disabled.
Configure the UserLock IIS Agent HTTP Module at the root level of IIS
(as documented at the beginning of this article).Specify IIS Application Pools to monitor:
By default, when you configure the IIS agent on an IIS website, all applications from this site are monitored independently of the application pool they run on.
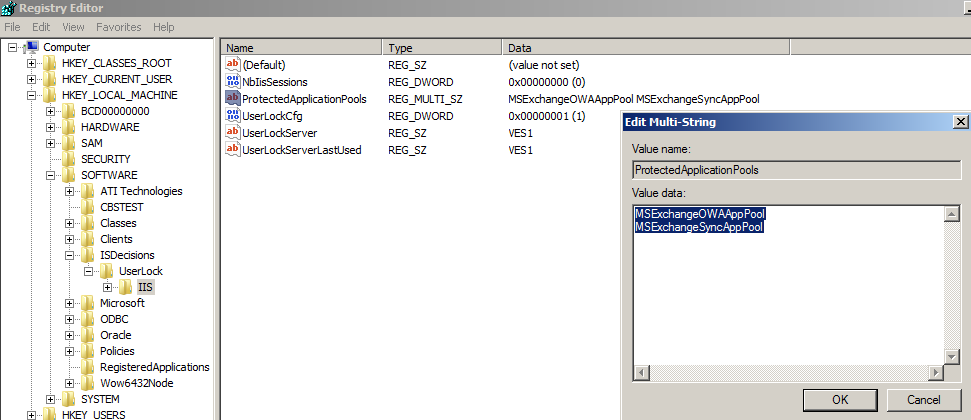
If needed, you can choose to monitor only Web applications running on specific application pools by creating the following registry value (REG_MULTI_SZ type) on the IIS server:
HKEY_LOCAL_MACHINE\SOFTWARE\ISDecisions\UserLock\IIS\ProtectedApplicationPoolsThen enter the list of all application pools you want to supervise (one per line).
On an Exchange server for example, many Web applications are created on the 'IIS Default' website. If you configure the UserLock 'IIS agent' for this site, UserLock will display a lot of IIS sessions.
In most cases, you only want to control sessions from 'Outlook Web Access' and ignore the other Web applications. You can do this by specifying only “MSExchangeOWAAppPool” as application pool to monitor.
If you are interested in Active Sync, add “MSExchangeSyncAppPool”.
Example with both “MSExchangeOWAAppPool” and “MSExchangeSyncAppPool” application pools:
Advanced settings
If you want to exclude the sessions generated by Health Mailbox accounts, please configure advanced settings "IgnoredLocalUsers" and / or "IgnoredUsers".