MFA settings
This page details the global MFA (Multi-Factor Authentication) settings for UserLock. These options apply to all user accounts for which MFA is enabled.
Note
To access this page, go to Server settings ▸ MFA.
You need at least read permission on Server settings to view this page.
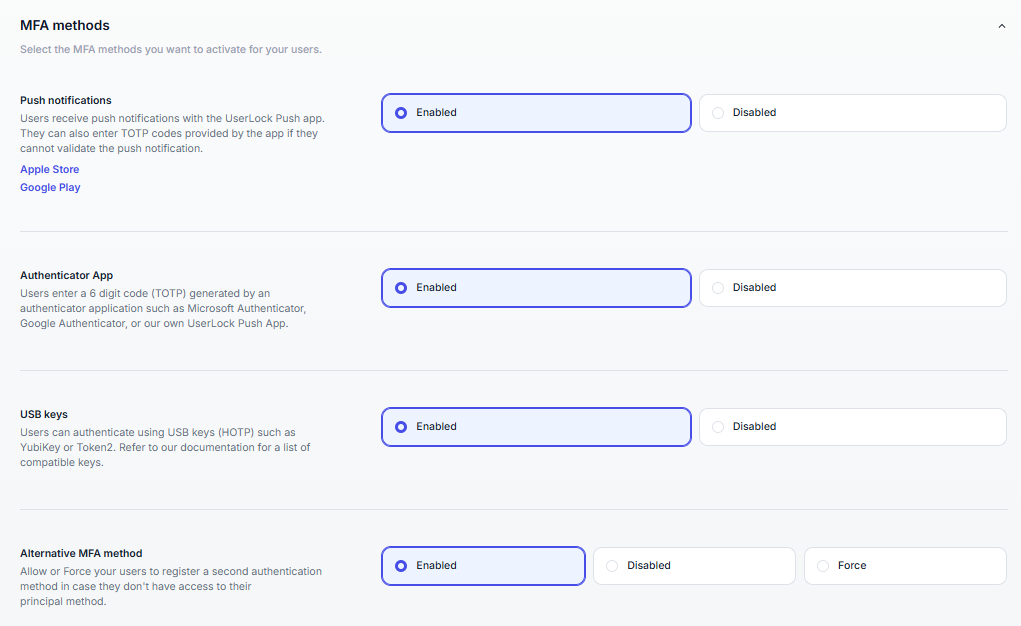
Select which MFA methods are available to users.
Multiple methods can be activated at the same time to increase flexibility and security.
Method | Description |
|---|---|
Push notifications | Requires the UserLock Push mobile app (iOS/Android). Users receive a prompt on their smartphone to approve or deny login attempts. |
Authenticator App | Compatible with any TOTP-based app (e.g., Google Authenticator, Microsoft Authenticator, Authy). Users enroll by scanning a QR code and then use a time-based code for each login. |
USB keys |
|
Alternative MFA method | Allows or forces users to register a secondary MFA method in case the primary one is unavailable. |
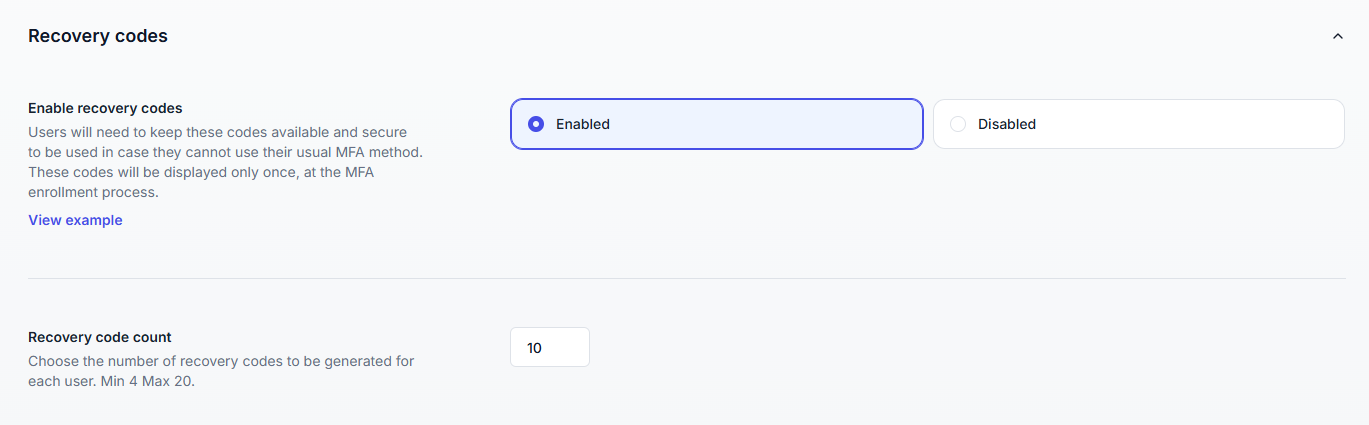
Provide users with backup access when their primary MFA method is unavailable.
Each user receives a set of single-use codes (between 4 and 20) during MFA enrollment.
Codes are generated automatically and must be stored securely by the user.
Each code can only be used once and acts as a temporary substitute for the second factor.
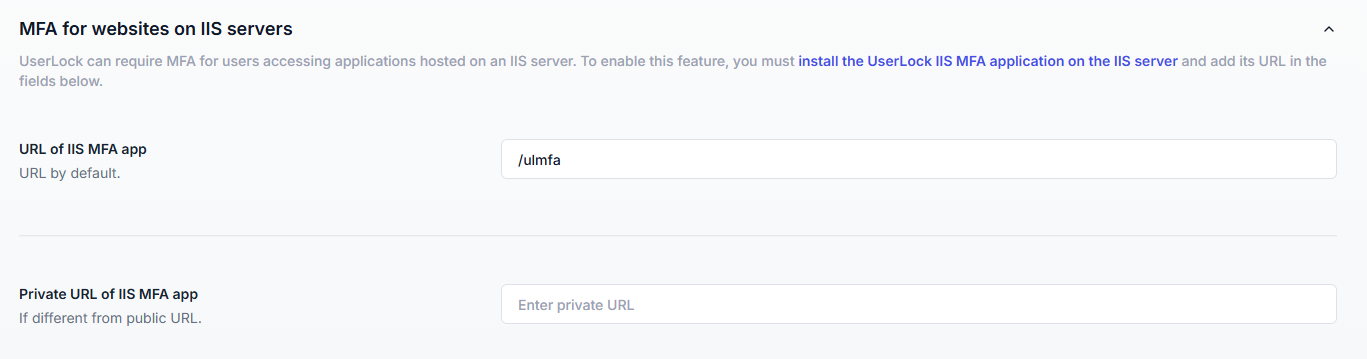
UserLock can enforce MFA for web applications hosted on Microsoft IIS using its integrated UserLock IIS Agent.
Adds a second layer of authentication after Windows authentication without modifying the application itself.
Users are prompted for MFA based on configured policies.
The IIS Agent must be installed and configured on the web server.
MFA must be enabled for the targeted users in UserLock.
Useful resources
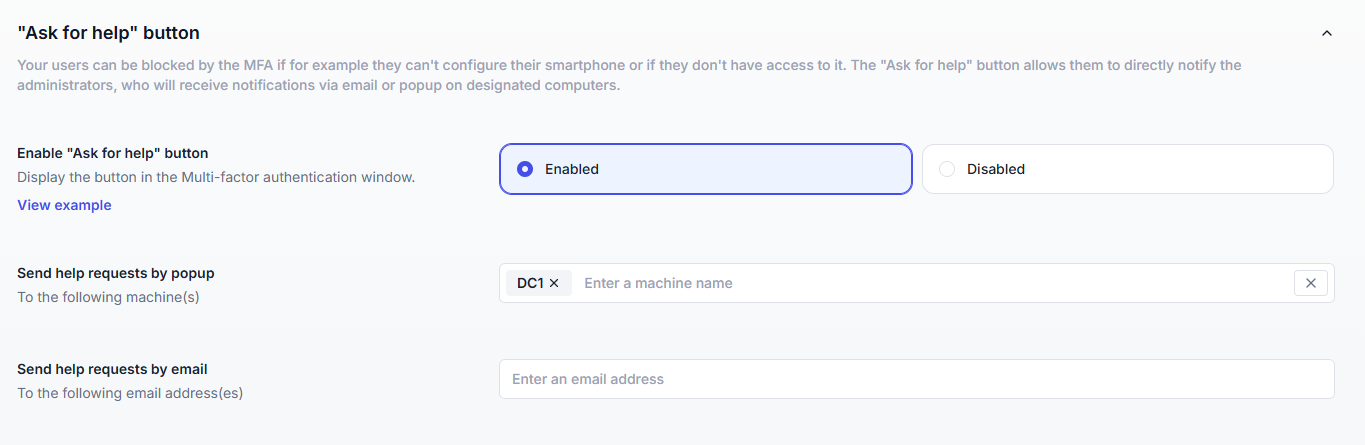
The Ask for help button lets users request administrator assistance if they cannot complete MFA verification (e.g., lost device, no network access).
This option is available directly on MFA prompts and during enrollment.
Sends a notification (email or popup, depending on configuration) to UserLock administrators.
Admin recipients can be defined manually (via LDAP search for machine names or email addresses).
Requests appear on the MFA help requests page in the Activity section, where administrators can:
Temporarily disable MFA for the user.
Reset the user’s MFA configuration.
Mark the request as resolved once the issue is handled.