Database
UserLock audits and stores in a database all user session activities on machines where the agent is deployed, as well as all actions and configurations performed by UserLock administrators. This history can be leveraged through UserLock’s reporting and analysis features.
Note
To access this page, go to Server settings ▸ Database.
You need at least read permission on Server settings to view this page.
This section displays some statistics about your database:
The number of records
The date and time of the first recorded event
The date and time of the last recorded event
The number of days the database has been in use
The installation package for UserLock includes a free Microsoft Access database file (named UserLock.mdb) to simplify evaluation and initial setup. This database is configured as the default storage for all audited events, but it is limited to 2 GB (structural limitation).
For production, we recommend using one of the following to ensure better retention and performance:
Microsoft SQL Express (maximum size 10 GB)
SQL Server (no theoretical size limit)
MySQL (driver installation required)
Note
For step-by-step instructions on how to configure UserLock with a production database, see the Production database setup guide.
In this section, select the appropriate options according to the database system you choose:
Option | Description |
|---|---|
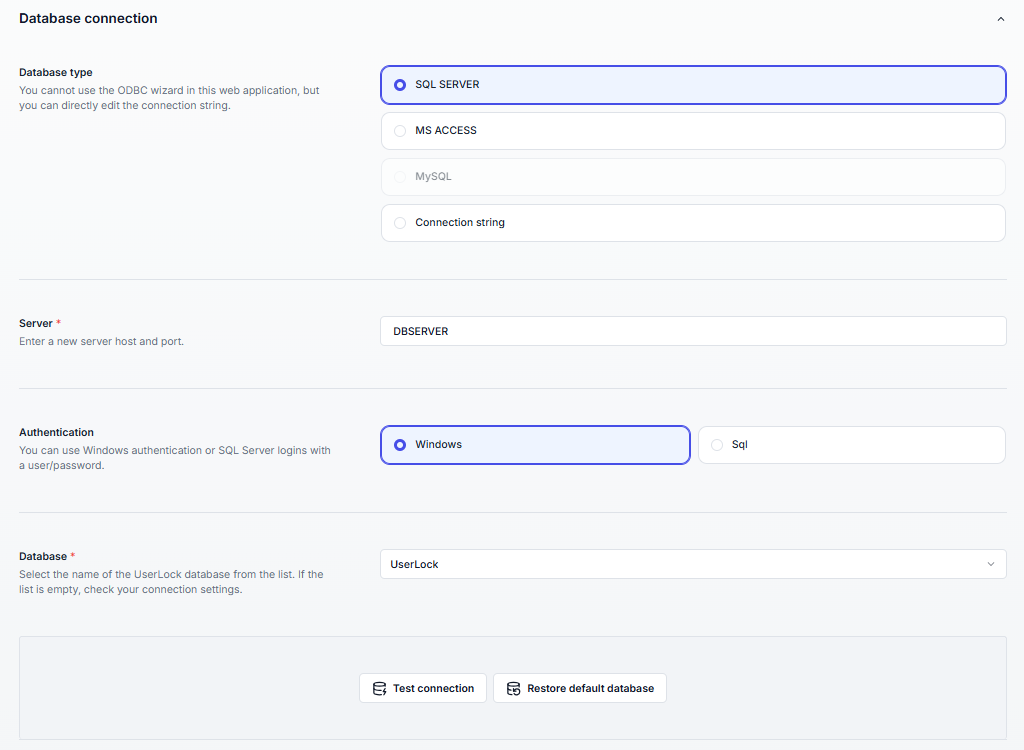
Database type |
|
Server | Enter the server name hosting the database. |
Authentication |
|
Database | Once the previous parameters are filled in, the list of available databases is loaded. Select the UserLock database you created. |
Note
Before saving, click Test connection to validate the settings (a toast message will confirm the result in the bottom-right corner).
⚠️ Tables are automatically created when the first events are recorded in the database (e.g., a lock/unlock event on a machine with the Desktop Agent installed).
The Restore default database button resets the configuration to use the default MS Access database.
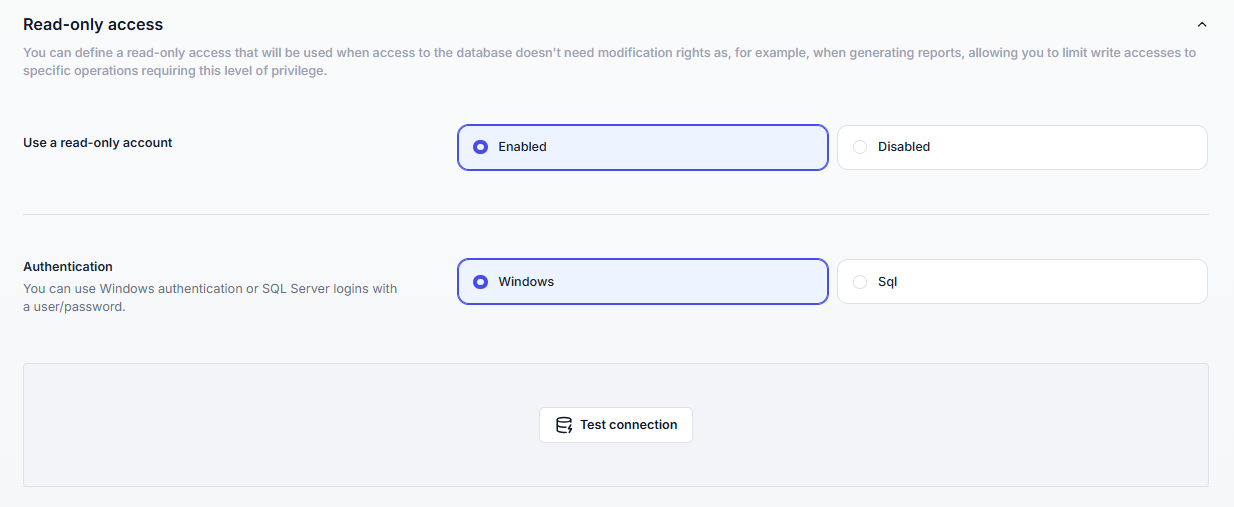
A second connection string with fewer privileges can be defined for read-only access.
This connection is used when no modification rights are required (e.g., generating reports), which limits write access to only those operations that need it.
Enable the option
Select the authentication mode (Windows or SQL)
Test the connection before saving
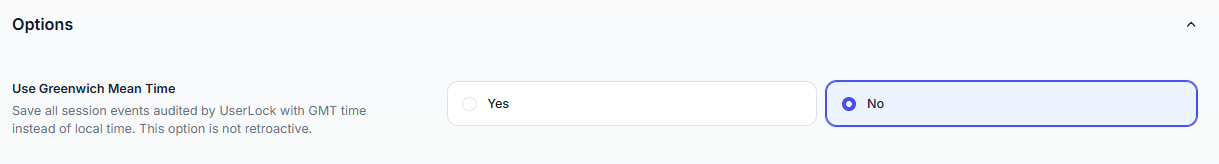
This option saves all audited events with GMT time instead of local time.
Note
⚠️ This option is not retroactive: events already stored will keep their original timestamps. Only new events will follow the newly selected mode.
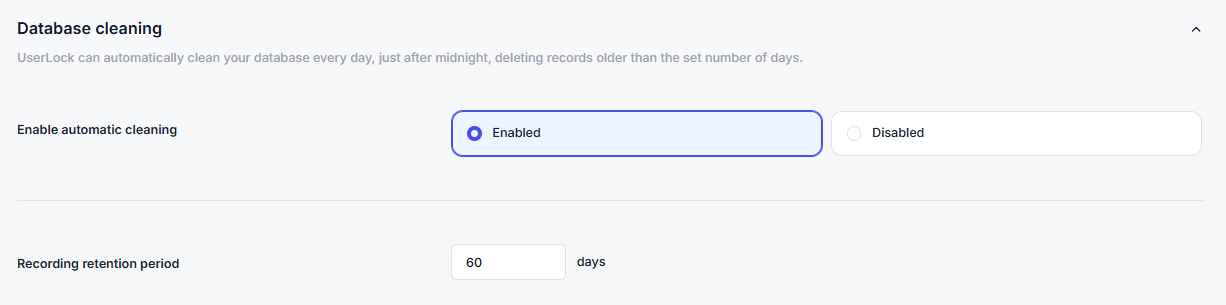
By default, UserLock keeps all events indefinitely in its database.
You can configure automatic cleaning to delete old logon events and prevent excessive database growth.
Enable the option
Specify the number of days to keep events
Every day just after midnight, older logon events are deleted
Note
⚠️ Cleaning operations are permanent and cannot be undone.
Always switch to SQL Express / SQL Server / MySQL for production. MS Access is only recommended for evaluation.
If you use a MySQL database or if you use the SQL Server authentication configure the read-only access to reduce risks of unwanted modifications.
Be careful with Database cleaning: deletion is permanent and irreversible. Always check your retention requirements before enabling it.
Regularly monitor database size and performance, especially if you store large session histories.
See also
💡 For background information on how UserLock uses its database, supported systems, and the internal schema, see Database architecture.